
Human Aspects of cyber Protection & PrivacY
Who are we?
We are a group of researchers discovering how to better protect people by understanding how humans interact with software. While we work on many areas of computer security, we primarily focus on the quickly evolving landscape of Machine Learning (ML), understanding how to defend against new forms of ML-enabled abuse, and how to harness ML-powered tools for security systems.
We use a combination of social science methods and software evaluation techniques. In human-subject work, we learn user perceptions with observational techniques (e.g., interviews/surveys) and discover how factors influence security with controlled experiments. In software, we use benchmarking techniques to rigorously compare systems. Combined, we holistically assess software security via technical and usable metrics.
Jaron Mink directs the Happy Lab at Arizona State University in the School of Computing and Augmented Intelligence.
Our lab is actively recruiting PhD students, master's students, and undergraduates! If you're interested in joining the lab, learn more here!
Recent News
-
2026-01-19: Work with the SEFCOM and TSP Lab has been conditionally accepted to CHI 2026, congrats all!
-
2025-09-22: A joint work with Lindsay Sanneman and Anil Murthy was accepted to NeurIPS LLM-Eval Workshop.
-
2025-06-17: Jaron and Tanusree from the GPSLab were recently awarded Google Research Scholar Grant for their proposal: Designing Accessible Tools for Blind and Low-Vision People to Navigate Deepfake Media
-
2025-05-19: We're exciting to welcome Ashely Ishoel and Harshit Mathur for their SURI internships!
Our Research Directions
Our work discovers how human interaction impacts ML security in two ways: How human factors can be 1) exploited to reduce security and 2) harnessed to improve security. Since ML-enabled abuse is becoming increasingly common, we investigate how lay users perceive and react to new attacks, e.g., how social media users react to deepfakes. As ML is beginning to be applied in security-critical systems, we evaluate how usable these tools are for technical users, e.g., how easy it is for ML developers to apply security defenses.
Mitigating Deceptive AI-Generated Content [1, 2]

AI-generated (AIG) content represents a pressing societal concern; it can be used to create fake personas or impersonate real persons to produce misinformation, conduct scams, or destroy reputations. As these attacks often rely on how real people perceive this content, understanding this perception is critical to understanding the harms of AIG content, and potential mitigations. Our lab researchs how people understand and perceive this emerging threat, as well as whether human-in-the-loop centered defenses are effective.
Integrating ML in Secure Systems [3, 4]
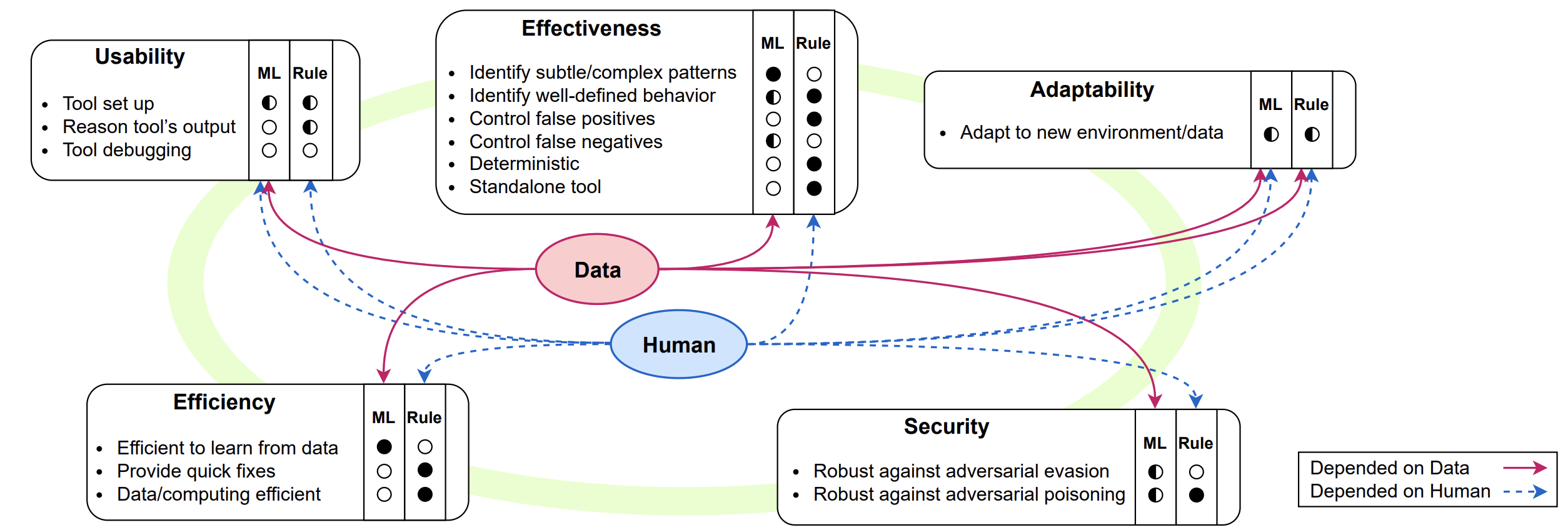
ML is increasingly being implemented in a variety of security-sensitive applications, with researchers often predicting practitioners’ needs and security concerns; however, little work has investigated the accuracy of these predictions, and the practical utility of these systems in the field. Our work bridges this gap by discovering what needs security and ML practitioners have in ML-enabled applications. Overall, our work discovers if academia's research agenda misaligns with practitioner requirements, ways to rectify them, and new paradigms for human-ML interaction in cybersecurity settings.
Accessible Cybersecurity Education [pwn.college]

We're excited to work with the SEFCOM Lab to improve and evaluate scalable cybersecurity education at pwn.college.
We're currently creating modules for practical adversarial machine lessons, discovering areas of improvement for courses, and improving personalized tutoring.
Additionally, we work on how to improve diversity and inclusivity in security research and cybersecurity workforce at large.
Want To Get Involved? Join Us!
School of Computing and Augmented Intelligence at Arizona State University
ASU Brickyard Engineering (BYENG), 699 S Mill Ave, Tempe, AZ 85281
Who are we?
We are a group of researchers discovering how to better protect people by understanding how humans interact with software. While we work on many areas of computer security, we primarily focus on the quickly evolving landscape of Machine Learning (ML), understanding how to defend against new forms of ML-enabled abuse, and how to harness ML-powered tools for security systems.
We use a combination of social science methods and software evaluation techniques. In human-subject work, we learn user perceptions with observational techniques (e.g., interviews/surveys) and discover how factors influence security with controlled experiments. In software, we use benchmarking techniques to rigorously compare systems. Combined, we holistically assess software security via technical and usable metrics.
Jaron Mink directs the Happy Lab at Arizona State University in the School of Computing and Augmented Intelligence.
Our lab is actively recruiting PhD students, master's students, and undergraduates! If you're interested in joining the lab, learn more here!
Recent News
- 2026-01-19: Work with the SEFCOM and TSP Lab has been conditionally accepted to CHI 2026, congrats all!
- 2025-09-22: A joint work with Lindsay Sanneman and Anil Murthy was accepted to NeurIPS LLM-Eval Workshop.
- 2025-06-17: Jaron and Tanusree from the GPSLab were recently awarded Google Research Scholar Grant for their proposal: Designing Accessible Tools for Blind and Low-Vision People to Navigate Deepfake Media
- 2025-05-19: We're exciting to welcome Ashely Ishoel and Harshit Mathur for their SURI internships!
Our Research Directions
Our work discovers how human interaction impacts ML security in two ways: How human factors can be 1) exploited to reduce security and 2) harnessed to improve security. Since ML-enabled abuse is becoming increasingly common, we investigate how lay users perceive and react to new attacks, e.g., how social media users react to deepfakes. As ML is beginning to be applied in security-critical systems, we evaluate how usable these tools are for technical users, e.g., how easy it is for ML developers to apply security defenses.
Mitigating Deceptive AI-Generated Content [1, 2]

AI-generated (AIG) content represents a pressing societal concern; it can be used to create fake personas or impersonate real persons to produce misinformation, conduct scams, or destroy reputations. As these attacks often rely on how real people perceive this content, understanding this perception is critical to understanding the harms of AIG content, and potential mitigations. Our lab researchs how people understand and perceive this emerging threat, as well as whether human-in-the-loop centered defenses are effective.
Integrating ML in Secure Systems [3, 4]

ML is increasingly being implemented in a variety of security-sensitive applications, with researchers often predicting practitioners’ needs and security concerns; however, little work has investigated the accuracy of these predictions, and the practical utility of these systems in the field. Our work bridges this gap by discovering what needs security and ML practitioners have in ML-enabled applications. Overall, our work discovers if academia's research agenda misaligns with practitioner requirements, ways to rectify them, and new paradigms for human-ML interaction in cybersecurity settings.
Accessible Cybersecurity Education [pwn.college]

We're excited to work with the SEFCOM Lab to improve and evaluate scalable cybersecurity education at pwn.college. We're currently creating modules for practical adversarial machine lessons, discovering areas of improvement for courses, and improving personalized tutoring. Additionally, we work on how to improve diversity and inclusivity in security research and cybersecurity workforce at large.